Integration of cybersecurity soutions
To meet your demands, AlgoSecure works with various outsiders and pragmatically innovative partners. These close relationships guarantee a global and efficient solution thanks to our operationnal expertise based on our consulting and engineering missions. Our interventions are made in total independance from editors.
We are focusing on three areas of integration:
- Secure bastion server: as a gateway for all infrastructure administration operations, this secure server allows, among other things, the sequestration of administration accounts, the recording of administration sessions, and the identification of administrators.
- Security in Industry 4.0: the industrial world is increasingly targeted by attacks, some of them very sophisticated, especially in the '4.0 era' where machines are connected to the Internet via the IoT for monitoring purposes.
- Active Directory security: Active Directory is an enterprise directory used within Windows networks. Its security is essential for the entire infrastructure, but is unfortunately often insufficient.
You can contact us so we can your security needs together.

Secure bastion server
In a corporate network, different security issues arise for the computer resource administration:
- Traceability: how to monitor and keep track of operations performed using high privileges on the servers?
- Privilege management: how to quickly add and revoke admin staff rights without having to reconfigure all servers?
- Decreasing attack surface: how to make sure that admin services are exposed only to administrators?
A bastion server makes it possible to respond to these problems, and therefore represents an undeniable asset for the security of a company network.
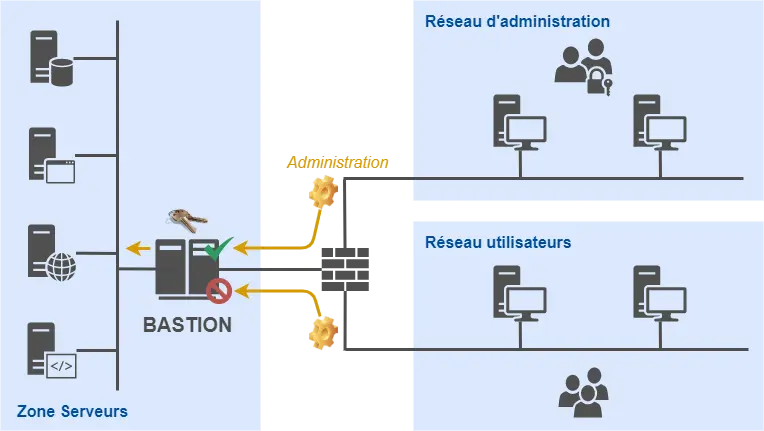
However, this is not a trivial thing to implement. There are many questions about the operational aspect of such a solution:
- How do we dimension the bastion server to allow it to perform its traceability functions?
- How do we architect the computer network so that resource administration goes through this server?
- How do we set up a workflow of approval and authorization processes from administrators to the resources protected by the bastion?
- How to solve the problem of maintaining the bastion in operational conditions over time and the evolution of the computer network?
Our experience in integrating this type of solution within different environments with several hundred administrators allows us to provide you with answers to the questions raised above, in order to minimize the complexity of integrating this element within your structure.
Security in Industry 4.0
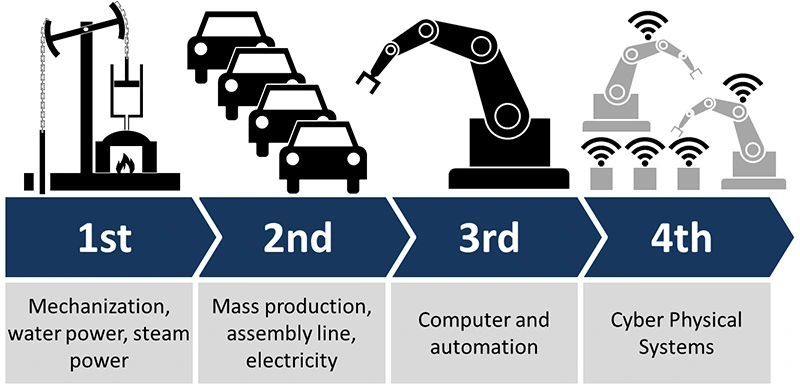
One of the defining components of Industry 4.0 is the integration of IoT and other digital technologies into industrial machines. This makes it possible to exploit the possibilities offered by big data, but also piloting and interfacing facilities with other systems. However, it does induce cyber risks that need to be taken into account in order not to leave the door open to attackers. (schema: C. Roser).
We can cite, among others, three threats that have targeted the industrial world over the last decade:
- Stuxnet (2010): This is the first known threat on the ICS. This worm was introduced by USB key on one of the laptops of an operator at the Iranian nuclear power plant in Natanz, from where it spread to the rest of the network, mainly targeting the Siemens branded PLC. Once introduced into the network, the worm spreads by exploiting default passwords and Windows vulnerabilities.
- BlackEnergy (2015): When the Ukrainian power grid was attacked, the city of Kiev suffered an hour-long blackout. This was the result of a large-scale attack targeting 30 power plants, during which the malware was triggered 6 months after the network was infected through phishing emails prompting the execution of an attached Office document macro.
- NotPetya (2017): Following WannaCry a few months earlier, this malware has spread to many companies and industries, exploiting a vulnerability in Windows systems and a lack of updates. Being a ransomware, it was later re-written as a wiper, in order to make the hard disk of the affected machines unrecoverable, even if a ransom was paid.
The industrial systems affected during these various attacks are equipped with software and protocols (Modbus, S7, OPC...) designed in the 1970-1980's and intrinsically vulnerable. It was the safety aspect, i.e. the physical security of people and facilities, which logically took precedence over the security aspect at the time. But this approach does not take into account the risk of computer compromise, and therefore the loss of availability.
To overcome these security defects, we offer you a range of services:
- a risk analysis of industrial environments
- an industrial systems security audit, mainly focused on the isolation of the most critical networks
- a service of SOC and monitoring of industrial systems
- a user awareness to gestures and procedures in industrial environments
In addition, we can share with you the fruits of our research on IoT security, including the development of a methodology and a tool for an assisted security assessment of an IoT ecosystem. We could then take advantage of a concrete industrial context to make this tool even more relevant.
Specialists in information security and pentest in Lyon, Paris, Saint-Etienne and throughout France
You've enabled "Do Not Track" in your browser, we respect that choice and don't track your visit on our website.