What's a ransomware?
Ransomware, also commonly referred to as "cryptolockers", after the most notorious of them, is a computer threat designed to make victims pay a ransom. Typically, they prevent access to the personal files of compromised users. A more recent variant, called "extorsionware", threatens to block access to online accounts, or release compromising personal data or videos.
Upon installing on a machine, the ransomware will encrypt the files one by one, making them unreadable and protected by a key that is passed to the ransomware operators. This key will only be given out for a ransom, usually paid for with a cryptocurrency such as Bitcoin. It allows operators to cover their tracks easily.
Ransomware thrives primarily on two factors.
- They are easy to spread There are many ways to run ransomware on a system. However, they all exploit a lack of technical safeguards and a lack of vigilance or computer literacy of the victims.
- They usually have a good success rate. Victims don't communicate about their experiences, so it's hard to get accurate statistics. Nevertheless, the fact that the ransom price is kept affordable, and the risk of file loss, push the victims to pay the ransom. This allows ransomware operators to continue their business.
Private individuals, companies and the industry are a target of choice for ransomware, as it was the case during the WannaCrypt outbreak.
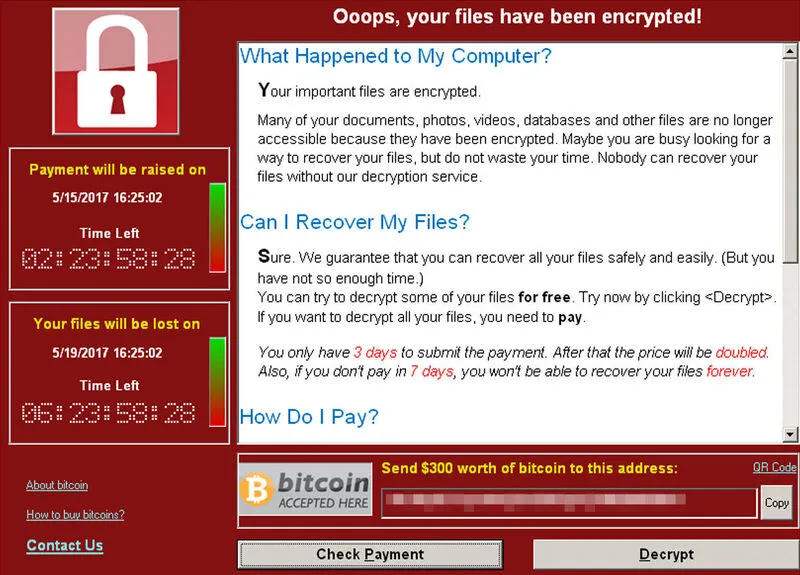
What can we do about ransomware?
As a first step, our recommendation is to analyze the situation with an expert, and not to pay the ransom. Paying ransom encourages these kinds of attacks, and provides financial income to criminal groups that also engage in other forms of crime. Nor is there any guarantee that the attacker will give you the key, or that you will be able to decrypt your files afterwards. This is the case of the PwndLocker/ProLock ransomware, which decryption tool sent by the attackers after the ransom was paid has a bug and doesn't decrypt files heavier than 64 Mo. A similar situation occurred with the Lorenz ransomware, for which the encryption process renders any file with a weight of multiple 48 bytes unreadable, even after decryption by their tool, and also allows decryption of any popular file type (Microsoft Office files, PDF files, as well as some types of image or video files) without paying the ransom.
Furthermore, with the development of extorsionware, ransomware operators may deliver the key... but ask you to pay an additional cost to not release your files publicly. This is the case of the ChaCha/Maze ransomware, for which attackers ask for two ranswoms: one of them for the decryption tool, the other one for not publishing stolen files.
Thus, paying ransom should be the last resort solution.
Not all ransomware is created equal: they are written by different developers, and like any computer program, some have flaws. Thus, depending on the type of ransomware, it will be possible in some cases to recover the files without paying the ransom, by exploiting a vulnerability in the ransomware. The NoMoreRansom site lists a list of decryption tools for certain ransomware.
Security researchers are working hand in hand to identify every ransomware, classify it, study it, understand how it works, and then if possible, come up with a free decryption tool for each ransomware. All the data from this research is put to the benefit of the ID Ransomware site, which allows, from a sample encrypted file, and the information note left by the ransomware, to know if it has a decryption tool.
Identify the ransomware that infected your computer
If the ransomware you've been infected with does not have a decryption tool, there are several solutions.
- If the immediate access to your data is critical, for example in the context of your company's business, you can certainly choose to pay the ransom, or else pay a specialized company that will analyze the functioning of the ransomware by reverse engineering. In either case, the success of the operation is not guaranteed. You should also be aware that the services of a specialized malware analysis company usually cost more than the ransom, and take longer to get a result. That said, the researchers' efforts could benefit all ransomware victims worldwide, not just you.
- If the immediate access to your files is not critical, we advise you to keep them safe. Don't worry, encrypted files are inert and do not carry any threats per se. In time, researchers may be able to find a way to decrypt the files. So you might get your files back in a few months or years, potentially free of charge.
Of course, the choices below only apply if you don't have any backups of your data. Which brings us to the question of what safeguards you could put in place to protect against this kind of incident in the future.
How do you protect yourself from ransomware?
Various measures can be implemented to protect you from this kind of computer threat.

- You can start by setting up a regular file backup process. In a business context, different solutions exist to back up all types of server services and technologies. For home user, it may simply be a matter of placing these files on a medium that remains disconnected from the computer and the network except during the backup process (hard disk and/or cloud storage).
- Ransomware sometimes exploit software vulnerabilities to break into machines. It is therefore advisable to keep your systems and applications up to date, mainly the operating system, and to systematically apply the security patches offered by the editor.
- Protection and surveillance software is becoming more and more sophisticated to combat these kinds of threats. We therefore advise you to keep an up-to-date antivirus program on your computer. Other types of programs, such as browser ad blockers, can also be used to limit certain threats on the web. These are typically banner ads warning you that your computer is infected, and offering you to download an antivirus program that is nothing more than malware such as ransomware. You have to choose an ad-blocker that is recognized by the community, because many of them are actually programs that are at best ineffective, at worst malicious. Our consultants recommend uBlock Origin.
- Finally, the most complicated point, but still one of the main vectors of infection: remain vigilant on the Internet, because the best and the worst are there. Systematically question the relevance of an email, especially when it contains an attachment or a link to a website, and it incites to perform certain actions. Is the sender really who he or she says he or she is? What is the sender's email address? What is the link pointing to? What is the attachment supposed to contain? Why do I need a password to unzip it? What is its extension? Why does this document ask for macros to be enabled? Do not hesitate to contact the sender through any other channel than email, and make sure the email is legitimate. For companies, our security awareness trainings are designed to familiarize users with security and help them acquire the right gestures, and thus reduce the probability of infection.
Generally speaking, protecting yourself from ransomware requires time and investment in skills and tools. So, is it worth it? It all depends on how important your data is to you, and how much time loss and stress you are willing to accept in the event of an infection.
You're infected with a ransom but aren't sure what to do? Don't hesitate to contact us, we'll do our best to help you.
Specialists in information security and pentest in Lyon, Paris, Saint-Etienne and throughout France
You've enabled "Do Not Track" in your browser, we respect that choice and don't track your visit on our website.