R&D

Here at Algosecure, Research and Innovation are of utmost importance for Algosecure.
Our employees can dedicate up to 10 days per year (we call them the Thinking Days!) to personal trainings or development projects, in parralel to their day-to-day missions.
We are also founding the preparation of 2 PhD thesis 'Cifre', in order to contribute to the understanding of the new technologies, as the Internet of Things (IoT) for instance.
Pollenisator

Pollenisator is a data aggregation tool for analyzing the output of tools used during a pentest. It allows to automate the different recognition tasks, using existing classical tools or internally developed tools and scripts.
Pollenisator has been developed in order to match the different use cases that the AlgoSecure team has during an audit: gathering of data, perimeter and timeframe restrictions, and notes sharing.
The parameters of the external tools can be customized by the auditors. They pre-fill the tools' command line, their priority, and the time slot if needed. Then, Pollenisator will complete the command line with the specific parameters of the target (port, service, version...) and start the scan whenever possible.
At the end, the results are then aggregated within the database to provide more information for the audit. Auditors can then sort, search and annotate relevant information from the database, for example:
- Which IPs have an open SSH port? What is the name and version of the service behind this port?
- What services have been annotated as "to be investigated" by the auditors?
Finally, the tool allows our team to fill out a list of defects and vulnerabilities found during the audit and assign them a criticity score. With Pollenisator, we can then generate an audit report based on a Word template, fully customizable by the auditors.
This is a true teamwork, created by our team and soon to be released under an open source license, accessible by clicking on the logo below:
Ph.D. Thesis on IoT security
Through this project lead by Jonathan, we try to evaluate the security of the smart device networks, by means of intrusion tests. After a phase of bibliographical research, we came to the conclusion that current tools and methodologies can not be used to efficiently drive penetration tests over smart device networks.
Rather than defining a new methodology dedicated to IoT, we focus on the evalutating the phases that differs between IoT or IT security assessment. We found the differences reside in the reckon phase, and the vulnerability analysis phase.
The goal of this project is to propose a tool that can assist during the various phase of a penetration test on IoT network. To do so, we are integrating a modelisation and a methodology into a framework that help assessing the security level of the IoT environment. Several articles from our blog (in French) present this project and its achievements in a more detailed manner.

Jonathan talks about his research during a MLSSI
Jonathan presented his research at the Pass-the-Salt 2020 conference, and the video and slides are available here (in English).
The legal status of penetration testing audits
Research and the advancement of security is of significant importance to AlgoSecure, which is why we are funding the work of our specialist in cybersecurity law. Since March 2019, she has been preparing a doctoral thesis in partnership with the Grenoble Legal Research Centre and thanks to the ANRT's CIFRE programme.
The field of computer security is, as we have all noticed, becoming more and more standardized. It is no longer only a question of technical and managerial skills at stake, but also, and increasingly, of various legal skills: technical standards (such as ISO 27001), RGPD, criminal law, public law, cyber insurance, cloud security... All of this requires that the legal knowledge be dynamically and harmoniously incorporated into the cybersecurity skills center. We have initially decided to internalize these legal skills within our team, with our full-time salaried lawyer. We have also decided to support her doctoral work in cybersecurity law to advance this area of expertise at the crossroads of technical and legal paths. Preparing a doctoral thesis in a company specialized in cybersecurity allows to to cumulate the advantages of the academic approach and field resources, for a more significant advance of the state of the art in this field.
This thesis has for title: "Hacking services, between legality and illegality. Its purpose is to determine the legal conditions under which the activities of penetration testing and red team operations can be continued in a lawful manner. The work in progress is currently studying in detail all aspects of criminal law relating to information system interference offences (computer intrusion, fraudulent maintenance, interference with the integrity of data or the functioning of the system, data theft...). It is only by fully mastering the elements constituting these infractions that it will be possible to compare the performance of external or internal intrusion tests, or even red team operations. This will then make it possible to detect the grey areas: those that are not legally defined, or that are legally defined in a contradictory manner.
The next step will be to look for remedies that would adjust criminal law and contract law into this context. These two branches of law do not initially pursue the same objectives, but they respond to different logics. Controlling legal risk in an economic field where the two are so closely intertwined may therefore prove more delicate.
This research is also, as a subsidiary and ancillary activity, an opportunity to study more widely the criminal risk of digital technology. Indeed, beyond the academic issues highlighted by the preparation of this doctoral thesis, many aspects of penetration testing services and red team operations raise questions of law. The active collaboration between our specialist in cybersecurity law and our pentesters team allows us to provide answers to these questions.
The resulting interdisciplinary expertise is being harnessed to enrich our approach to intrusion testing and reporting.
Bonware
Bonware is a botnet C&C platform developed by Algosecure for educational purposes. This tool tries to simulate as realistically as possible, and without damaging the targeted information system, the way a system can be attacked from a malicious botnet vector. The motivation behind developing our own botnet was to understand its inner workings, to have total control over it, and then to be able to demonstrate its dangerousness in order to raise awareness among users.
Indeed, many computer attacks are now based on botnets:
- Zeus (2010): infection by visiting a malicious website or by phishing emails, used for banking fraud
- Vawtrak (2013): infection by malicious Office attachments in phishing emails, used for banking fraud
- Dridex (2015): infection by malicious Office attachments in phishing emails, used for banking fraud
- Mirai (2016): infection by intrinsic vulnerabilities of connected cameras and the use of default passwords, used to perform DDoS attacks
A botnet is a set of bots or zombies computers (computers infected with malware) controlled by a botmaster on a C&C server (command and control). The botmaster must be able to propagate his commands to all bots in a fast way, and for this purpose, there are two botnet topologies:
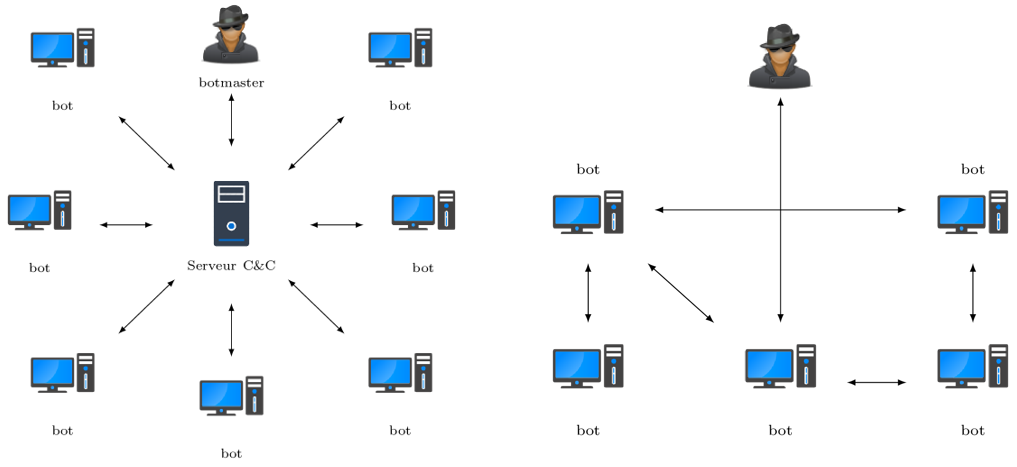
Each topology has its advantages and disadvantages:
| Topology | Conception | Detection | Latency | Mean survival time |
|---|---|---|---|---|
| Centralized | Easy | Average | Low | Low |
| Peer-to-peer | Hard | Low | Average | Average |
In addition, each bot must be able to exchange information with each other or with the C&C server, while passing corporate firewall solutions. So we have to choose communication protocols that are unlikely to be blocked in corporate environments, and three main candidates meet these criteria:
| Protocol | Use | Detection | Advantages | Disavantadges |
|---|---|---|---|---|
| IRC | Easy | High | Simple | Usually blocked |
| DNS | Hard | Low | Usually not monitored | Generate a lot of trafic |
| HTTPS | Easy | Average | Heavily used | Usually filtered |
Once the botnet is architected, we need to choose the infection vector (the means by which our threat will end up on the target machines) as well as the payload (the threat that will be executed on the machines). We have chosen to disseminate our BonWare through targeted phishing campaigns according to the context of our customers. Payload generation is probably the most complicated phase, since it requires regular monitoring of the malware signature databases and detection techniques implemented by protection solutions, the so-called 'cat-and-mouse game'. We've had to adapt the operation of BonWare over the years as the defenses have evolved.
To protect against this type of threat, we recommend the following lines of defense:
- use and update an antivirus solution on workstations and email servers
- disable the default execution of macros for Office documents
- integrating an IPS solution to detect and prevent malicious network communications
- user awareness trainings to teach users to remain vigilant when opening an attachment and running a macro
Specialists in information security and pentest in Lyon, Paris, Saint-Etienne and throughout France
You've enabled "Do Not Track" in your browser, we respect that choice and don't track your visit on our website.
