Your outsourced IT security with the
AlgoSecure center of expertise
Information systems are becoming increasingly complex and the stakes related to security increasingly high. The security of information systems requires a very good knowledge and a permanent watch of security technologies and associated tools. It also requires a thorough knowledge of legal and regulatory compliance requirements.
This complexity and these specialized skills are illustrated in particular by the number of business profiles. ANSSI has listed 16 of them in its panorama of cybersecurity professions.
In order to gain in security, AlgoSecure offers, with its Competence Center, to outsource part or all of the competences dedicated to the security of your information systems.
How does it work?
A project manager and a team of experts are appointed, and decide with you on a roadmap of SSI missions for the year. The project manager acts as the interface between your needs and our teams: a one-stop shop. A certain number of days are integrated to gain flexibility (unexpected topics, research, crisis management).
Who is it for?
Our Competence Center is aimed at:
- structures that do not have dedicated cybersecurity skills,
- CISOs who need operational support,
- structures that need a transitional CISO,
- structures that wish to call upon an outsourced CISO.
 =======
=======
 >>>>>>> 85f6e5f15622efd1a44c94c534ec1af74593d22d
>>>>>>> 85f6e5f15622efd1a44c94c534ec1af74593d22d
The benefits of our Competence Center
A one-stop shop (outsourced CISO) with a pool of skills
The project manager is your privileged contact. He is in charge of gathering experts according to your needs, piloting and acting the right levers to secure your information systems.
Behind him is a team of experts. Our consultants are selected for their experience, qualifications, and suitability for your projects. The composition of the team can evolve to adapt to new issues.
A tailor-made program thanks to an à la carte support
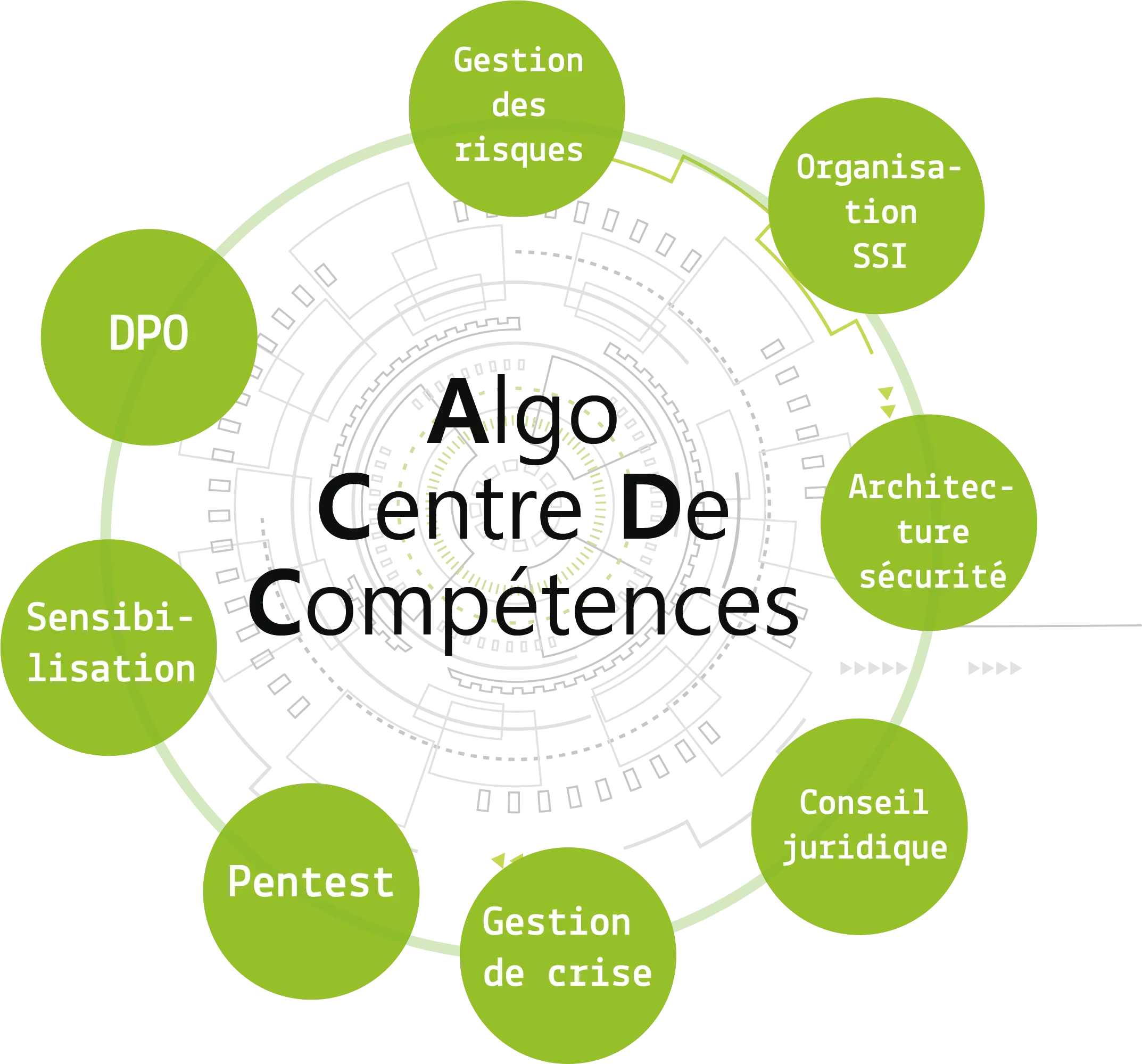
Our center brings together all the skills needed to secure information systems: the risk management, ISS organization, security architecture, consulting, legal, crisis management, pentests, security trainings of employees, as well as data management via outsourced DPO services (Data Protection Delegate).
Our Competence Center makes it possible to supplement the competences of your internal team or a complete accompaniment thanks to AlgoSecure's pool of competences.
A continuous service for more serenity, available 365 days a year
Our Competence Center assures you a serene accompaniment. Our employees take turns ensuring continuous service and dealing with any unforeseen circumstances. In the event of an attack, your outsourced CISO activates a crisis cell capable of quickly dispatching experts to your facility.
A controlled budget, reduced and optimized costs
The budget is defined on a yearly basis. You control your budget by including your approach to securing and managing your information systems. All cybersecurity skills are combined in a single provider allowing both economy of scale and simplified HR procedures. We generally offer accompaniments by 3-year contracts.
Outsourcing your IT security through our Competence Center allows you to meet your real needs; you only pay for what you need.
Our Competence Center process
A Dedicated Project Manager (outsourced CISO) is appointed at AlgoSecure. With skills in security organization and project management, they will orchestrate the Competence Center.
The Diagnosis phase consists of taking account of the current situation and building the foundations of what will be your support. This involves:
- Getting to know the existing situation (PSSI, IT charters, etc.);
- A macro risk analysis of the global environment;
- Co-building of KPIs and a steering dashboard (we hate watermelon indicators);
- The creation of a priority action plan (PAP);
At the end of this phase, the Competence Center starts up, and will cyclically and independently run the following three phases.
The Assessment phase consists of planning regular audits to verify the overall security of the various perimeters making up the information system:
- Risk analysis of critical business applications
- Phishing test to evaluate the staff's level of knowledge
- Intrusion test on the internal infrastructure
- WiFi penetration test
- SCADA penetration test
- IoT penetration test
- Configuration audit
- GDPR audit
- Organizational audit
- Social Engineering audit
- Red Team audit
The Remediation phase consists of accompanying the partner to secure its information system.
The following actions can be performed during this phase:
- Drafting of an Information System Security Policy (ISSP)
- Drafting of a Disaster Recovery Plan (DRP)
- Drafting of a Business Continuity Plan (BCP)
- Drafting of a Backup Plan
- Drafting of a Patch Management Policy
- Drafting of Records of Processing Activity (in a GDPR context)
- Implementation of the ISS management plan
- Accompaniment and follow-up of the various remediation actions suggested during the evaluation phases
- Training of users to good ISS practices
- Assistance to the project owner to select the adequate security measures
- Project management assistance for the definition of the various cybersecurity requirements for your partners or during the drafting of specifications
- Drafting of specifications to include SSI requirements
The continuity phase consists of monitoring and being ready to react in case of external attacks.
The following actions can be performed during this phase:
- Improving and consolidating the SSI dashboard
- Communication and reporting of SSI progress to the organization's management bodies
- Review of the different controls and updates of the different remediation actions
- Integration of cybersecurity in each project as part of an in-depth security approach
- Recurrent risk analysis
- Vulnerability watch on the partner's equipment
- Provision of an incident response team according to your needs
- Post-attack forensic analysis
- Legal watch
Other pages that might interest you :
Security audits and pentests
We audit your information systems to reveal vulnerabilities: these are our penetration testing engagements.
Security audits and pentests
We audit your information systems to reveal vulnerabilities: these are our penetration testing engagements.
Risk analysis
We help you evaluate the risks that are cast on your systems, and establish a plan in order to deal with these risks.
Specialists in information security and pentest in Lyon, Paris, Saint-Etienne and throughout France
You've enabled "Do Not Track" in your browser, we respect that choice and don't track your visit on our website.