PCI DSS compliance
With the rise of digital services and online payments, the issue of transaction security has become unavoidable. Fraud and cyberattacks targeting banking data are becoming increasingly common, and companies must therefore be extra vigilant in protecting their customers' sensitive information. It is precisely in this context that the PCI DSS standard comes into play, a security framework designed to help organizations better secure credit card data.

The PCI DSS standard
The PCI DSS (Payment Card Industry Data Security Standard) is an international security standard developed by the major payment card brands (Visa, Mastercard, American Express, Discover, and JCB). It aims to prevent fraud and leaks of sensitive data by securing credit card data during collection, processing, storage, and transmission.
The PCI DSS standard applies to any organization—merchant, service provider, payment gateway, data center—that stores, processes, or transmits payment card data. Compliance with this standard is mandatory.
The PCI DSS standard and its requirements
The PCI DSS standard comprises 12 general requirements:
- Install and maintain network security controls
- Apply secure configurations to all system components
- Protect stored account data
- Protect cardholder data with strong encryption during transmission over open public networks.
- Protect all systems and networks against malware
- Develop and maintain secure systems and software
- Restrict access to system components and cardholder data on a need-to-know basis
- Identify users and authenticate access to system components
- Restrict physical access to cardholder data
- Log and monitor all access to system components and cardholder data
- Regularly test the security of systems and networks.
- Supporting information security with organizational policies and programs
PCI DSS pentests
The purpose of penetration testing within a PCI DSS environment is to assess the protection of card data across the systems and networks connected to it. It must be performed at least once a year on the entire application and network architecture, and whenever there is a significant change (new service, infrastructure migration, critical update), meeting the 12 requirements.
It should be noted that the PCI DSS standard establishes requirements rather than a single methodology for achieving compliance. This leaves room for interpretation on many points, often depending on the auditor—the Qualified Security Assessor (QSA) and the specific context of each company.
Therefore, it is important to be supported by a specialized and experienced service provider and to have high-quality deliverables.
The AlgoSecure methodology
Definition of the PCI-DSS scope
The PCI DSS standard poses several challenges, the first of which arises at the preliminary stage: defining the scope of the audit. This step is essential, as an ill-defined scope compromises the relevance of the tests performed.
At AlgoSecure, we begin each PCI DSS engagement with a scope identification and validation phase. This includes:
- All applications, services, hosts, and infrastructure exposed on the Internet
- Internal components interconnected with the card processing environment
- The card processing environment (CDE: Cardholder Data Environment)
Tests definition
Once the scope has been defined in collaboration with your technical teams and your CISO, the test sets to be performed are determined. All tests performed are designed to assess the compliance of your information system with the 12 requirements of the latest version of the PCI DSS standard.
As mentioned, the PCI DSS standard offers a certain degree of interpretation that may be specific to each QSA (Qualified Security Assessor) in charge of your audit.
For example, in the area of “Management of data encryption and cryptographic suites used”, the PCI DSS standard will challenge the entire chain, both in terms of highly complex technical aspects (with requirements 4.x and 12.3.3) and complex organizational processes (with requirements 3.6.x and 3.7.x).
The auditors' role is to test the IS, but also, and above all, to explain in detail the various non-conformities identified during in-depth technical and organizational discussions. This ongoing dialogue between AlgoSecure auditors and your internal teams is essential not only for correcting discrepancies, but also for establishing sustainable security governance in line with industry best practices.
Agile pentesting
Faced with the growing number of tests to be performed, whether mandatory annual assessments or audits triggered by major changes to the information system (application version upgrades, firewall replacement, network architecture upgrades), AlgoSecure offers an “agile” pentest approach.
Thanks to the expertise acquired through testing and our growing knowledge of your IT system, our teams are able to maximize the efficiency and accuracy of testing. Each new campaign builds on the history of previous analyses, enabling better risk anticipation, more detailed coverage of attack scenarios, and optimized response times.
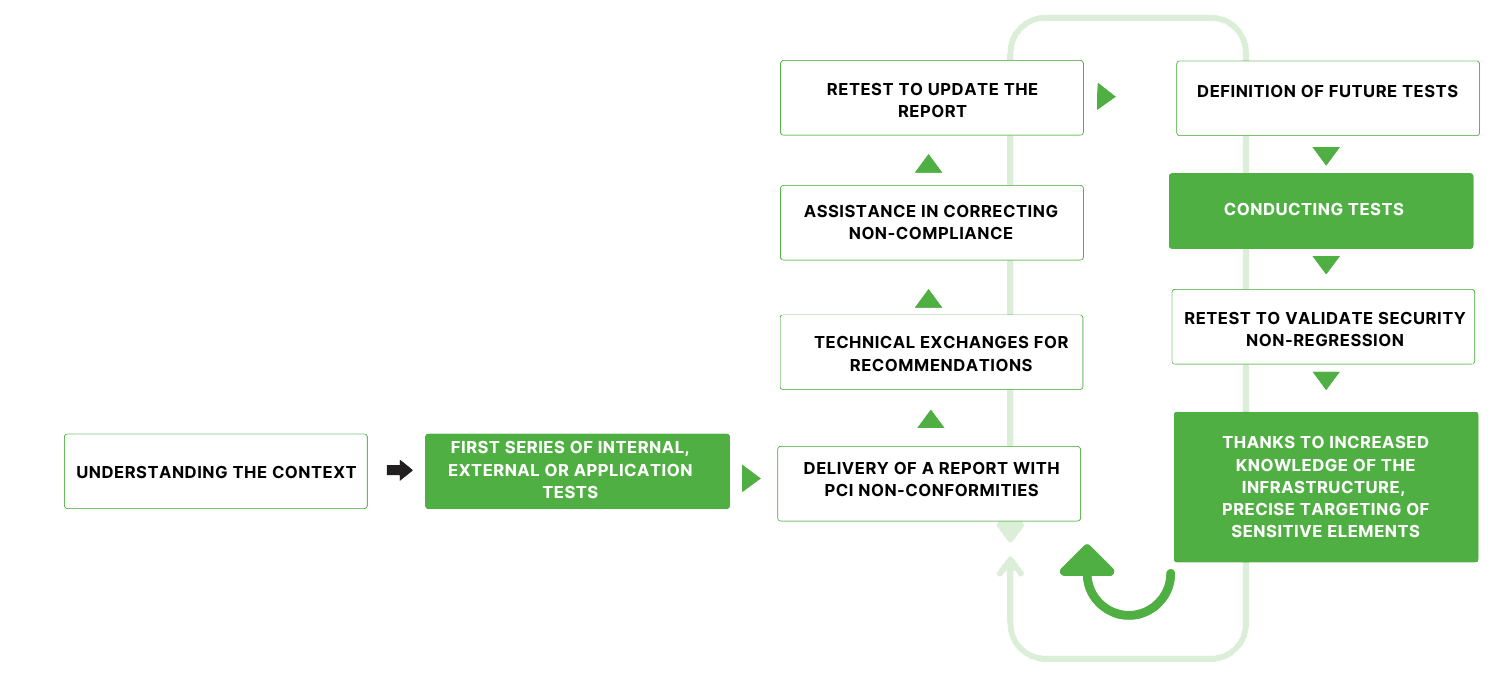
This approach also makes it possible to streamline exchanges, capitalize on existing tools and processes, and adapt testing campaigns to the actual lifecycles of your assets. It therefore fits naturally into a DevSecOps or continuous security governance approach.
The first line of defense: segmentation tests
Among the mandatory tests for PCI DSS compliance, network segmentation tests play a fundamental role. They enable verification that the CDE card processing environment is properly isolated from the rest of the information system, particularly from areas deemed “unsafe.”
These tests must be performed every six months, and also systematically after any significant change to the network architecture, such as the addition of a DMZ, the creation of new VLANs, or migration to a cloud infrastructure.
Their purpose is to validate the effectiveness of segmentation mechanisms such as firewalls, access control lists (ACLs), VLANs, and SDN architectures. Their objective is to ensure that certain parts of the network have no possible access to the CDE, thereby reducing the risk of intrusion.
The test procedure is based on an empirical approach. The AlgoSecure auditor connects to a selection of internal VLANs representing non-CDE zones as well as VLANs that are part of the CDE. Attempts are then made to communicate between each segment, testing different protocols (ICMP, TCP, UDP) to identify open flows.
Every communication between a VLAN and a service located in another VLAN is analyzed to determine the legitimacy of the traffic. In the event of undocumented or suspicious flows, discussions are held with the technical teams to understand their origin and necessity. A complete flow matrix, accompanied by a technical explanation for each opening observed, is then produced and transmitted.
This process fits naturally into our agile approach: an initial set of tests is carried out during the main audits, followed by a second set six months later, requiring less effort thanks to the knowledge already acquired about your environment.
Segmentation testing is therefore a first line of defense, essential for ensuring effective separation between critical components and other parts of your network, reducing the attack surface to a minimum.
The PCI-DSS V4.0 standard is 400 pages long, but that's not all!
Although PCI DSS compliance represents a significant amount of work, it is not simply a “regulatory” barrier; above all, it is a guarantee of increased IT security, acting as a real lever of trust for your customers and partners. By combining a systematic approach to pentests, continuous monitoring, and robust governance, you can anticipate risks and secure your payments against current and future threats.
To set up a customized penetration testing program and ensure your PCI DSS v4.0 compliance, contact our team of security experts.
Going further: thinking about security beyond PCI DSS
While the PCI DSS standard provides a solid foundation for securing payment data, it does not cover the entire information system. In fact, the entry points exploited by attackers often lie outside the PCI DSS perimeter, particularly in user networks, office environments, or development systems.
These areas, although outside the PCI scope, represent potential attack vectors that can be used to rebound to the cardholder data environment (CDE). That is why it is strongly recommended that you supplement your PCI DSS compliance efforts with more comprehensive offensive security measures, such as:
- Red Team campaigns to test detection and response to advanced attacks;
- phishing tests targeted to assess user awareness;
- workstation security audits and cloud environments or DevOps.
This 360° approach allows you to go beyond simple compliance and adopt a mature, proactive, and continuous security posture. PCI DSS then becomes a foundation—solid but not sufficient—on which to build a comprehensive, resilient cybersecurity strategy aligned with today's threat realities.
PCI requires training for developers working on the PA DSS perimeter (applications used in the CDE). AlgoSecure is able to provide this training.
Other pages that might interest you :
Red Team Audit
We test the security of your building and your staff based on scenarios we conceive with you.
AlgoLightHouse
Launch of our new AlgoLightHouse offering at Big Boss on November 16 and 17, 2023
SWIFT infrastructure audit
We audit your SWIFT infrastructure and its compliance with the Customer Security Controls Framework.
Specialists in information security and pentest in Lyon, Paris, Saint-Etienne and throughout France
You've enabled "Do Not Track" in your browser, we respect that choice and don't track your visit on our website.