Intégration
Afin d'élargir ses compétences, Algosecure collabore de manière pragmatique avec différents partenaires innovants, leaders ou challengers, selon les besoins de chaque client. Ces relations étroites permettent de vous assurer une solution globale et efficace grâce à notre expertise operationnelle appuyée par nos missions de conseil et d’ingénierie. Nos interventions s'effectuent en toute indépendance vis à vis des éditeurs.
Nous nous concentrons sur trois domaines d'intégration :
- Serveur bastion sécurisé : point de passage obligé pour toutes les opérations d'administration de l'infrastructure, ce serveur sécurisé permet d'assurer, entre autres, la séquestration des comptes d'administration, l'enregistrement des sessions d'administration, et l'identification des administrateurs.
- Sécurité de l'industrie 4.0 : le monde industriel est de plus en plus visé par des attaques, certaines très perfectionnées, d'autant plus à « l'ère 4.0 » où les machines sont connectés à Internet via l'IoT à des fins de supervision.
- Sécurité de l'Active Directory : l'Active Directory est un annuaire d'entreprise utilisé au sein des réseaux Windows. Sa sécurité est primordiale pour toute l'infrastructure, mais est malheureusement souvent insuffisante.
Vous pouvez nous contacter afin d'étudier ensemble vos besoins.

Serveur bastion sécurisé
Dans un réseau d'entreprise, différentes problématiques de sécurité se posent pour l'administration des ressources informatiques :
- Traçabilité : comment surveiller et garder une trace des opérations effectuées à l'aide de privilèges élevés sur les serveurs ?
- Gestion des privilèges : comment ajouter et révoquer rapidement les droits du personnel d'administration sans avoir à reconfigurer tous les serveurs ?
- Diminution de la surface d'attaque : comment s'assurer que les services d'administraton soient exposés seulement aux administrateurs ?
Un serveur bastion permet de répondre à ces problématiques, et représente donc un atout indéniable pour la sécurité d'un réseau d'entreprise.
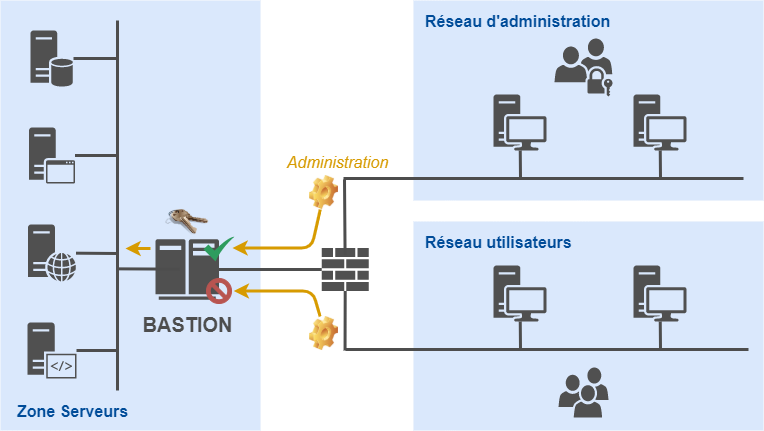
Il s'agit cependant d'un élément qui n'est pas trivial à implémenter. De nombreuses questions se posent sur l'aspect opérationnel d'une telle solution :
- Comment dimensionner le serveur bastion pour lui permettre d'assurer ses fonctions de traçabilité ?
- Comment architecturer le réseau informatique pour que l'administration des ressources passe par ce serveur ?
- Comment mettre en place un workflow de processus d'approbation et d'habilitation des administrateurs aux ressources protégées par le bastion ?
- Comment résoudre la problématique du maintien en conditions opérationnelles du bastion au fil du temps et de l'évolution du réseau informatique ?
Notre expérience d'intégration de ce type de solution au sein de différents environnements comportant plusieurs centaines d'administrateurs nous permet de vous fournir des réponses aux questions soulevées ci-dessus, afin de minimiser la complexité d'intégration de cet élément au sein de votre structure.
Sécurité de l'industrie 4.0
L'une des composants qui définit l'industrie 4.0 est l'intégration de l'IoT et autres technologies du numérique sur les machines industrielles. Cela permet d'exploiter les possibilités offertes par le big data, mais également des faciltés de pilotage et d'interfaçage avec d'autres systèmes. Toutefois, cela induit des risques cyber qu'il est nécessaire de prendre en compte afin de ne pas laisser la porte ouvertes aux attaquants (schéma : C. Roser).
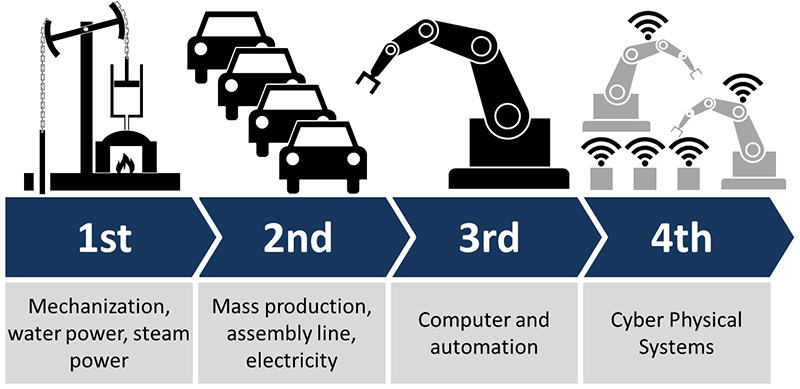
Nous pouvons citer entre autres trois menaces ayant ciblé le monde industriel au cours de la dernière décennie :
- Stuxnet (2010) : il s'agit de la première menace connue sur les ICS. Ce ver informatique a été introduit par clé USB sur l'un des ordinateurs portables d'un opérateur de la centrale nucléaire iranienne de Natanz, à partir duquel il s'est répandu sur le reste du réseau, ciblant principalement les PLC de marque Siemens. Une fois introduit dans le réseau, le ver se propage en exploitant des mots de passe par défaut et des vulnérabilités Windows.
- BlackEnergy (2015) : lordque le réseau électrique ukrainien a été attaqué, la ville de Kiev a subit une coupure d'électricité d'une heure. Il s'agissait du résultat d'une attaque d'ampleur visant 30 centrales électriques, durant laquelle le malware a été déclenché 6 mois après l'infection du réseau au travers d'emails de phishing incitant à l'exécution d'une macro d'un document Office en pièce-jointe.
- NotPetya (2017) : faisant suite à WannaCry quelques mois auparavant, ce malware s'est propagé à de nombreuses entreprises et industries, en exploitant une vulnérabilité des systèmes Windows et d'une absence de mise à jour. S'agissant d'un ransomware dans un premier temps, il a par la suite été ré-écrit pour se transofmrer en wiper afin de rendre le disque-dur des machines touchées irrécupérables, quand bien même une rançon aurait été payée.
Les systèmes industriels touchés au cours de ces différentes attaques sont équipés de logiciels et protocoles (Modbus, S7, OPC...) conçus dans les années 1970-1980 et intrinsèquement vulnérables. C'est l'aspect sureté, c'est à dire les sécurité physique des personnes et des installations, qui a logiquement primé sur l'aspect sécurité à l'époque. Mais cette approche ne prend pas en compte les risques de compromission informatique, et donc de perte de disponibilité.
Pour pallier à ces défauts de sécurité, nous vous proposons un ensemble de services :
- une analayse de risques des environnements industriels
- un audit de sécurité des systèmes industriels, principalement orienté sur l'étanchéité des réseaux les plus critiques
- un service de SOC et de supervision de systèmes industriels
- une sensibilisation des utilisateurs aux gestes et procédures dans les environnements industriels
Par ailleurs, nous pouvons vous faire profiter du fruit de nos recherches sur la sécurité de l'IoT, visant entre autres à développer une méthodologie et un outil d'évaluation assistée de la sécurité d'un écosystème IoT. Nous pourrions ainsi profiter d'un contexte industriel concret pour rendre cet outil encore plus pertinent.
Spécialistes en sécurité informatique et pentests à Lyon, Paris, Saint-Étienne et partout en France
Vous avez activé l'option "Do Not Track" dans votre navigateur, nous respectons ce choix et ne suivons pas votre visite.


